KEY TAKEAWAYS
- Skimming involves the unauthorized capture of financial data or cash receipts for personal gain, often remaining undetected until victims notice unauthorized transactions or financial discrepancies.
- There are different types of skimming, including sales skimming, where employees pocket unrecorded cash transactions; receivables skimming, where payments intended for businesses are intercepted; and credit card skimming, using devices to capture card data at transaction points.
- The practice exploits trust in financial systems and human interactions, demanding vigilance and understanding to mitigate its impacts on businesses and individuals alike.
Understanding Skimming in Finance
Definition and Scope
Skimming in finance involves the illegal capture of information, typically through technological means, to commit theft from credit cards or other personal data. It’s a subset of embezzlement where small, unnoticeable amounts are extracted over time. While initially applied to theft of small sums of cash from a business before it is recorded, skimming has evolved with technology, primarily targeting electronic transactions. The scope of skimming spans both personal and corporate financial realms, affecting millions of individuals annually and costing businesses significant revenue.
Historical Context
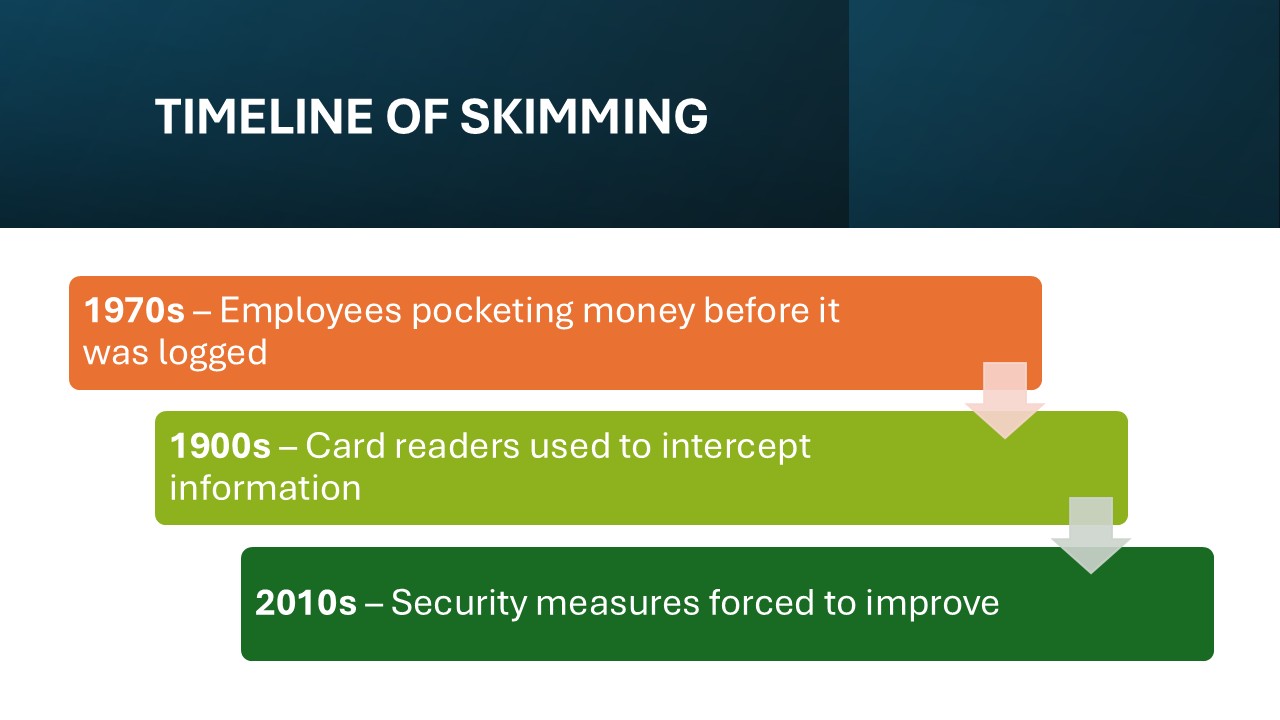
Skimming fraud has a history dating back to the pre-digital era when businesses dealt predominantly in cash. Originally, it involved employees pocketing money before it was logged into official accounts. As electronic transactions became the norm, skimming adapted, with criminals developing more sophisticated methods like using card readers to intercept information. Over the decades, several high-profile cases have demonstrated how technology-driven skimming can seriously impact both individuals and corporations globally, forcing improvements in security measures.
The Mechanics of Skimming
How Skimming Works
Skimming operates by stealing financial information during either a transaction process or at a point where the cardholder might not notice tampering. Typically, criminals install small devices known as skimmers on ATMs, gas pumps, or point-of-sale (POS) terminals. These devices capture data from the magnetic stripe of a card as it’s being swiped or inserted. As a preventative measure, conducting regular inspections for any suspicious activity around payment terminals and card slots is crucial. More recently, some devices can wirelessly transmit this information to the criminals, often through Bluetooth signals. In addition, some skimmers use hidden cameras or fake keypads to capture PIN numbers, leading to further skimming crimes. Skimming cash receipts, especially in retail scenarios, is also scrutinized as it can be linked to tax evasion practices. This covert process results in unauthorized access to accounts and potentially, significant financial loss for victims.
Common Techniques Used by Criminals
Criminals employ various techniques to execute skimming fraud effectively. One prevalent method is the use of overlay skimmers, which fit snugly over existing card readers, capturing data without alerting users and often stealing the card slot details. Another technique involves internal skimmers, which are installed inside card readers and are harder to detect. Cloning, where the stolen data, including the personal PIN number, is used to produce counterfeit cards, is a common follow-up action to skimming. Criminals might also employ Bluetooth or other wireless technologies to retrieve data from skimming devices without needing to return to the scene, showcasing a level of technological expertise. These strategies evolve constantly, challenging security systems to stay a step ahead.
Additionally, in merchant locations, fraudsters might engage in skimming cash receipts, a white-collar crime where cash is stolen before it is recorded, often as a form of tax evasion. Verification mechanisms such as audits can help detect and prevent these activities. Price skimming, although not commonly associated with fraud, is an example of how pricing strategies can evolve similarly.
Types of Skimming Fraud
Personal Finance Impact
Skimming can have a devastating impact on personal finances. When criminals gain access to your account details, they can make unauthorized withdrawals, leading to direct financial losses. Beyond losing money, victims often face the hassle and stress of resolving fraudulent charges with financial institutions. The time spent rectifying such issues, monitoring accounts, and ensuring personal information security could be significant. Moreover, there’s a psychological impact as the sense of financial security is compromised. It’s crucial for individuals to stay vigilant, regularly review account statements, and immediately report any suspicious activities.
Business-Related Instances
For businesses, skimming can lead to both financial loss and reputational damage. As a form of white-collar crime, skimming cash receipts is often utilized as a method of tax evasion by underreporting cash transactions. When skimming occurs within an organization, it might be perpetrated by employees or through compromised POS systems. Such incidents not only result in monetary losses but can also erode customer trust, especially if sensitive customer data is compromised. Handling skimming fraud involves significant investigation and recovery costs; plus, businesses might face legal penalties if they fail to secure customer data properly. Compliance officers play a crucial role by conducting regular audits to identify patterns indicative of skimming. Ensuring robust security protocols and regular audits are essential in minimizing these risks.
Examples of Accounting Skimming Fraud
Accounting skimming fraud involves the illegal diversion of funds before they are recorded in accounting systems, a practice that evades detection in financial records. Skimming cash receipts, a form of white-collar crime, is often employed for tax evasion due to its under-the-radar nature. Common examples include employees skimming cash from daily sales before entries are made, or creating fictitious refunds. Additionally, false expense claims exploit loose oversight in expense account approvals. A notable historical case involved a manager at a retail chain skimming daily receipts, amounting to losses exceeding $100,000 over several years. These scenarios underline the necessity for vigilant record-keeping and regular audits to catch anomalies before they snowball into significant losses.
Identifying the Warning Signs
Red Flags for Personal Accounts
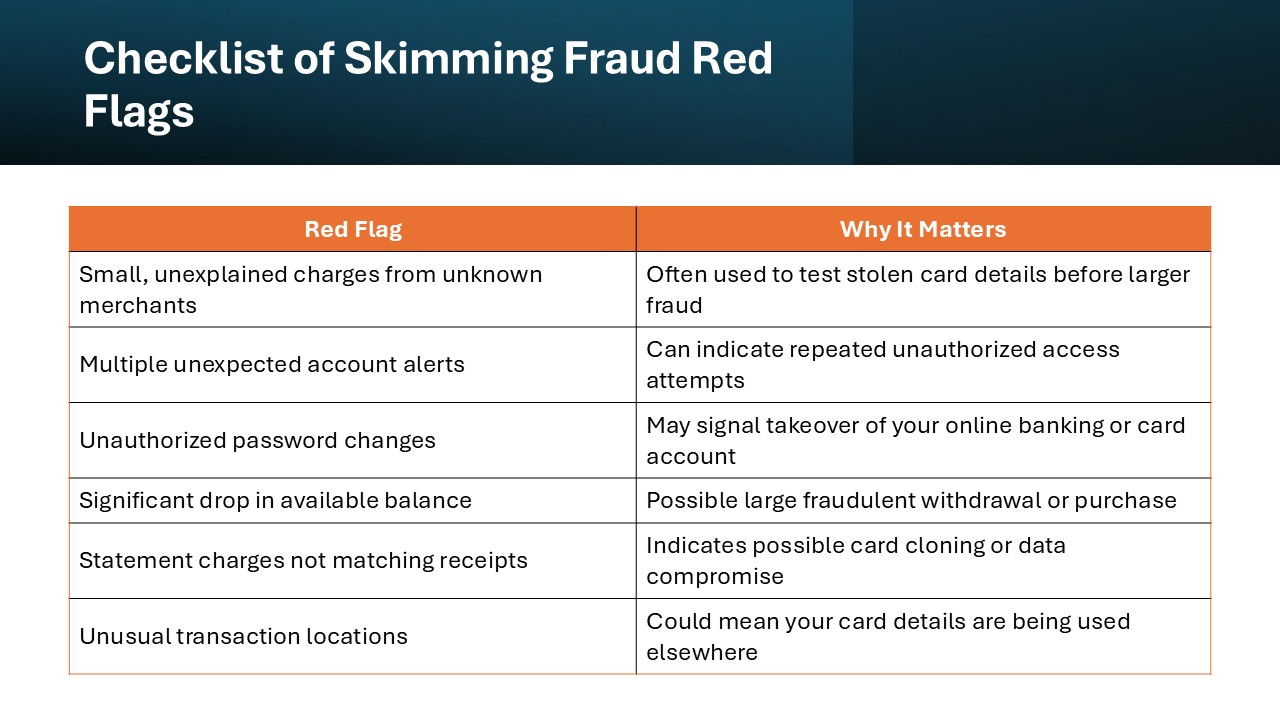
Identifying red flags in personal accounts can help catch skimming fraud early. Be wary of unexplained transactions or small charges from unfamiliar merchants, as criminals often test the legitimacy of the card. Regular receipt of multiple account alerts or unauthorized account password changes might also indicate compromise. Additionally, if you notice a significant decline in your available balance without corresponding spending, it’s crucial to investigate further. Staying proactive by monitoring statements and setting up transaction alerts can help minimize potential damage.
Warning Indicators for Businesses
Businesses should be on the lookout for several warning indicators that may suggest skimming activities. Discrepancies between recorded and actual cash or transaction volumes often signal internal issues. Frequent customer complaints regarding unknown charges or extended transaction processing times can also be indicative of compromised systems. Unusual employee behavior, such as reluctance to take leave allowing for others to review and reconcile accounts, is another red flag. Implementing robust monitoring systems and conducting regular audits can effectively detect these issues early on.
Real-life Examples and Case Studies
Notorious Skimming Incidents
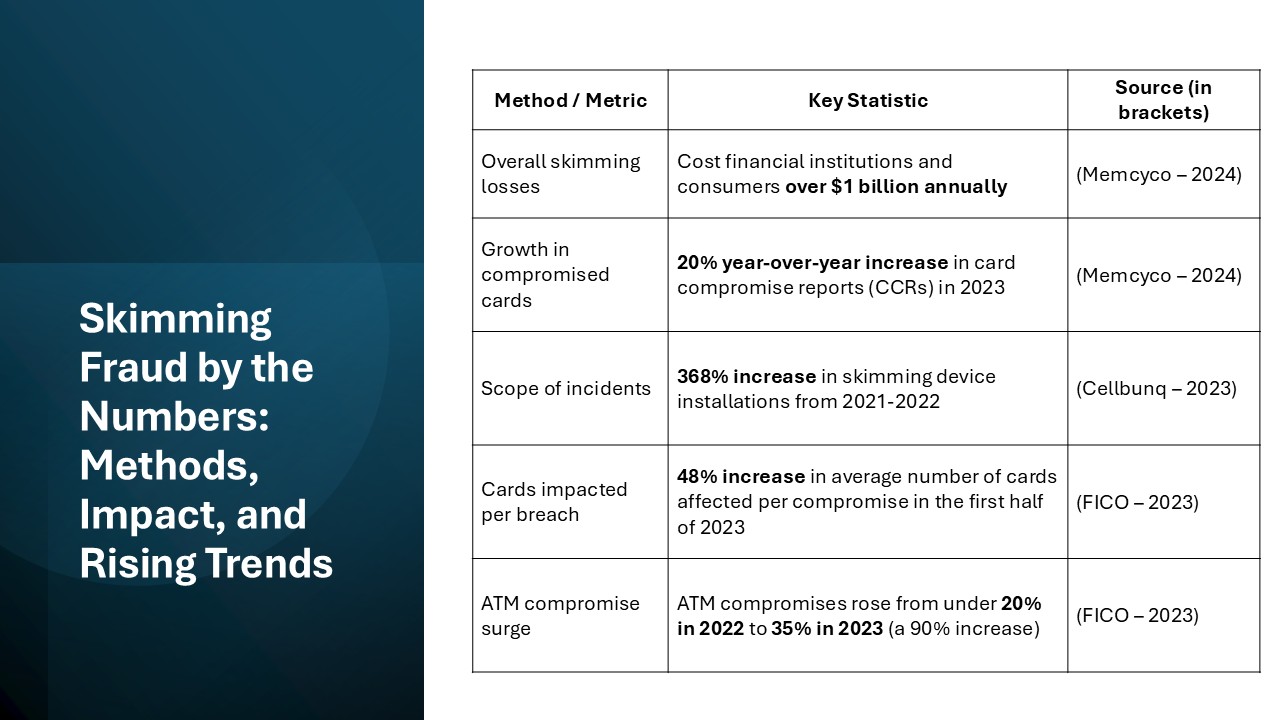
Over the years, several high-profile skimming incidents have captured headlines, underscoring the pervasive threat of this fraud. One notable case involved a large retail chain where criminals installed skimming devices on self-checkout terminals, compromising thousands of credit cards. In another incident, a global ATM skimming scheme affected numerous banks, costing over $1 billion in fraudulent withdrawals. These cases highlight the sophisticated tactics fraudsters employ and the vast networks often involved. Learning from these events, both individuals and businesses are urged to continuously update their security measures.
Lessons Learned
The lessons from infamous skimming incidents emphasize the necessity of staying vigilant and constantly evolving security practices. Businesses learned that regular audits and employee training are crucial for early detection and prevention. For individuals, it’s clear that consistent monitoring of account statements and utilizing updated financial security tools are essential defenses. These incidents also highlighted the importance of cross-industry collaboration, where financial institutions, law enforcement, and governments work together to develop proactive strategies against skimming. Promoting awareness campaigns can significantly reduce the impact of such fraudulent activities.
Protecting Against Skimming
Measures for Individuals
Individuals can take several proactive measures to safeguard against skimming. First, regularly monitor your financial statements and set up transaction alerts to catch unauthorized charges early, ensuring accessibility to your financial activities. Use contactless payment options or digital wallets, as they offer added security layers and convenience compared to traditional card swipes. When using ATMs, inspect the machine for any unusual attachments or loose parts before inserting your card. It’s also wise to update passwords frequently and enable multi-factor authentication for online banking platforms, which provides verification of your identity. Staying informed about the latest scams can further aid in recognizing and avoiding potential threats.
Security Practices for Businesses
Businesses can enhance their security against skimming through a multi-faceted approach. First, investing in advanced POS systems with EMV technology reduces the risk of card cloning. Regularly inspecting these systems for tampering, a key aspect of robust fraud prevention, is essential. Employee training on spotting suspicious behavior and securely handling transactions is crucial. Implementing encryption and tokenization for data security adds another robust layer. Moreover, retailers can use dedicated website modules for training to bolster staff knowledge effectively. Additionally, businesses should schedule routine audits to verify cash receipts align with sales records and work with financial institutions to stay informed about emerging fraud tactics and remedies.
Regulatory Landscape and Compliance
Current Regulations
Current regulations regarding skimming and financial fraud emphasize robust security measures and accountability. The Payment Card Industry Data Security Standard (PCI DSS) outlines comprehensive requirements for entities processing card transactions, mandating secure handling and storage of card information. Many regions have also enacted laws requiring businesses to report data breaches promptly to authorities and affected individuals. Regulatory bodies such as the Federal Trade Commission (FTC) in the U.S. continuously update guidelines to address emerging threats. These regulations aim to safeguard consumer data while enhancing businesses’ accountability for maintaining secure transaction environments.
Future Trends in Regulation
Future trends in regulation are set to focus on fortifying data protection and adapting to new technological advancements. As skimming techniques become more sophisticated, regulations will likely evolve to encompass data gathered through advanced payment methods like mobile wallets and cryptocurrencies. Cross-border collaboration may increase, with international standards being developed to address variation in regulations globally. Additionally, stricter compliance requirements for real-time reporting and enhanced data visualization tools for anomaly detection could become standard. Such trends will encourage businesses and individuals to invest in cutting-edge security technologies.
FAQs
What is the meaning of skimming in Finance?
In finance, skimming refers to the illegal act of capturing information from credit cards, debit cards, or cash transactions to commit theft. This often involves using devices called skimmers, which are secretly attached to card readers at points of sale or ATMs to steal data without the cardholder’s knowledge.
What should I do if I suspect skimming?
If you suspect skimming, immediately contact your bank or card issuer to report the suspicious activity and temporarily freeze your account. Review recent transactions for unauthorized charges and change your account passwords. Consider placing a fraud alert on your credit report with major credit bureaus to protect against further identity theft.
How can businesses safeguard their POS systems?
Businesses can safeguard their POS systems by implementing advanced EMV technology to reduce skimming risk. Regularly inspect and maintain terminals for tampering, and ensure encryption and tokenization are used for data security. Train employees on security protocols, and conduct routine audits to detect anomalies quickly. Partner with reputable payment processors to stay updated on threats.
Is online banking vulnerable to skimming?
Online banking is less vulnerable to traditional skimming, which typically targets physical card readers. However, it can be susceptible to other forms of data theft like phishing and malware. Use strong passwords, enable multi-factor authentication, and avoid accessing banking sites on public Wi-Fi to enhance security. Regularly monitor accounts for unauthorized activity.
What are skimming devices?
Skimming devices are illicit tools used to steal card information during a physical transaction. They are often attached discreetly to legitimate card readers on ATMs or POS terminals. These devices capture the card’s magnetic stripe data, enabling criminals to clone the card. They may also include hidden cameras or fake keypads to record PINs.
What is a skimmer device and how does it work?
A skimmer device is a covert gadget criminals attach to card readers on ATMs or point-of-sale terminals. It works by copying the data from a card’s magnetic stripe as it’s swiped or inserted. Some skimmers are paired with cameras or fake overlays to capture PINs. This stolen information is then used to create counterfeit cards or conduct unauthorized transactions.